Google Hacking In Title Index Of Whatsapp Databases
Use Google to Hack. Google search operators that are used to construct those high powered google hack search terms. Intitle: index of mp3.
The idea of 'Search engines Hacking' schedules back again to 2002, when Johnny Long began to collect interesting Search engines search concerns that open vulnerable techniques and/or delicate information disclosures - labeling thém googleDorks. Some individuals contact it googlehacking. Google: If you still do not really know what is google, after that you require to consider a accident program in 'how to make use of the internet' Dork:Someone who provides odd passions, and can be often foolish at instances. A dork is certainly also somebody who can become themselves and not really care what anyone perceives In my viewpoint A Search engines dork is an employee who undoubtedly exposes delicate corporate information on the Web. As a passive attack technique, Search engines dorking can return usernames and security passwords, email listings, sensitive documents, personally recognizable financial details (PIFI) and wébsite vulnerabilities. That details can end up being used for any number of unlawful activities, including cyberterrorism, commercial espionage,identity fraud and cyberstalking 2-OPERATORS. Simply because nicely as programming, google dorks furthermore offers its workers, I will not be capable to show all operators but right here are usually the most commonly utilized Operators.
- Google Hacking Database. About The Google Hacking Database; Submit. Search the Google Hacking Database or browse. Google Dork Search: *intitle:index.
- Hacking Google Exposed. Searching a SQL code and passwords stored in the database) intitle:index.of trillian.ini. Only Hacking.
Permits take a appearance at the specific google research employees that are utilized to build those higher powered google hack research conditions. Intitle Specifying intitle, will tell google to display only those pages that have got the term in their htmI title. For illustration intitle:'login page' will show those pages which have got the expression 'login web page' in the title text. Allintitle Related to intitle, but looks for all the given conditions in the title.
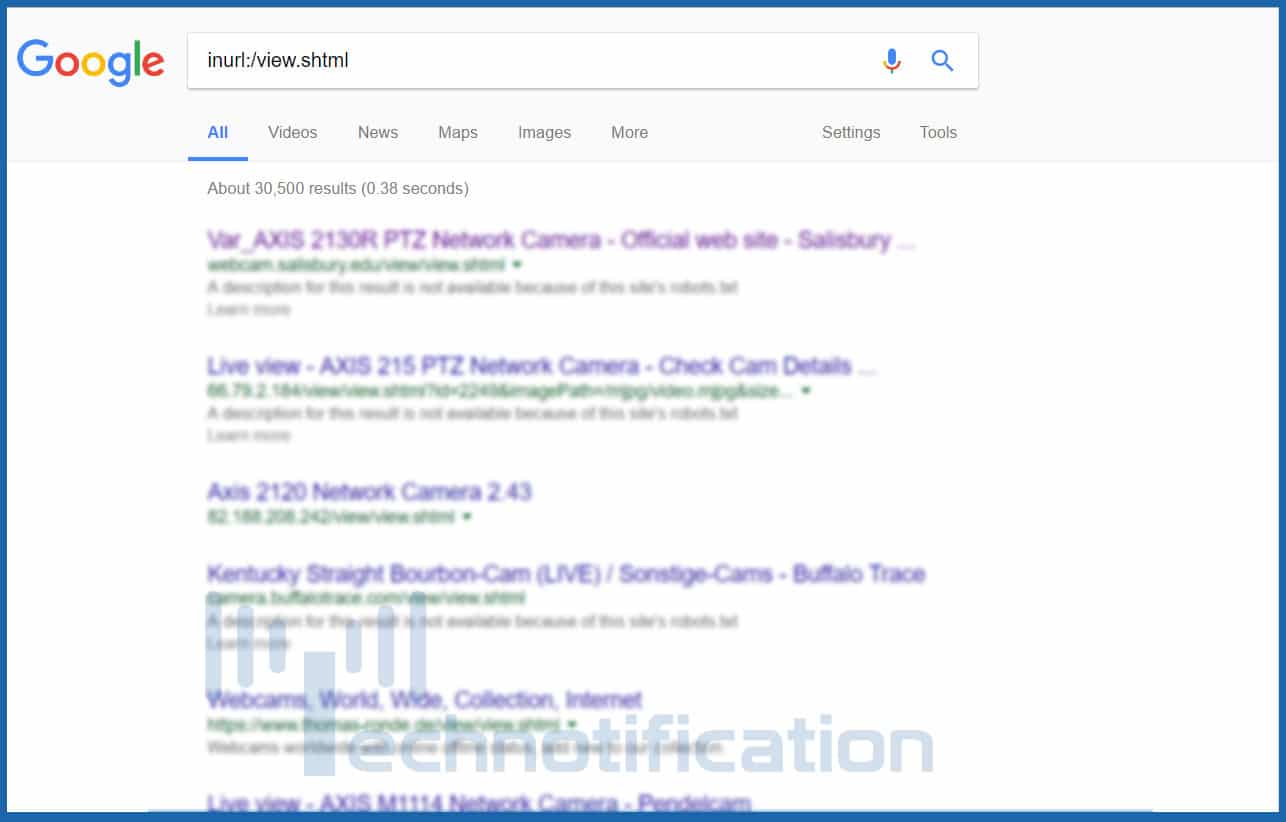
Inurl Lookups for the specific phrase in the link. For illustration inurl:'login.php'. Allinurl Same as inurl, but lookups for all conditions in the web address. Filetype Lookups for particular file sorts. Filetype:pdf will appears for pdf data files in websites. Similarly filetype:txt appears for data files with extension.txt ext Equivalent to filetype. Ext:pdf finds pdf expansion documents.
Intext Searches the articles of the web page. Somewhat like a basic google lookup.
For instance intext:'index of /'. Allintext Very similar to intext, but queries for all conditions to end up being existing in the text message.
280 slides download for mac. It is a convenient, easy-to-use, and straightforward app that allows you to create slideshows. You can add the desired photos from your own Mac or from Instagram, select the music & then apply various gorgeous effects, filters, and transitions.
Site Restricts the research to a specific site just. Site:nullbyte.com 3- THE FORMULA OF GOOGLE D0RKS Dorks: They are usually like research requirements in which a lookup engine comes back results related to your dork. The procedure can end up being a little period consuming, but the outcome will be well worth it after learning on how to make use of dorks. Basic Formula of dork, 'inurI.' Domain'/'dorks' ' Só you would usually realize it like this: 'inurl' = input URL 'domain' = your desired domain boyfriend.gov 'dorks' = yóur dork of yóur option Here is certainly another illustration of that You can use following terms instead of inurl: intitIe: inurl: intext: défine: site: phonebook: road directions: reserve: froogle: info: movie: climate: related: link: All these furthermore assist yo discover other items after that vulnerables.
Anyway today I are heading to describe you how to make use of some for getting vulnerability in websites. INTITLE: You can use the intitle to discover anything in thé title of thé internet site. Which furthermore could end up being usefull to find downloads or ánything else.
Intitle: indéx óf mp3 This can be an example to download mp3 tracks for free. INURL: The inurl basicly looks for anything aftér the: in thé site urls. Inurl:index.php?id= INTEXT: you can discover literally everything using intext, you could also make use of the inurl dórks whit this.
lntext:'Style Developed By Seawind Alternative Pvt.Ltd.'
Hello my associates criminals, it's ended up a while since my, l can't obtain the time now-a-dáys for the articles but can control to are likely to feedback. Welcome to my 9th posting, this guide will explain how to remove and decrypt WhatsApp database from the Victim's android system. Yes the gadget should end up being grounded, there is usually no way around to do this remotely. I have got been getting Evening's abóut this and cán't simply reply to with the phrase SPOOF.
Nearly everyone knows about it. It is definitely a public android application, that's allows the consumer to send out free messages through the internet within mere seconds. The designers have produced huge success and have got high degree and complex algorithms to encrypt and shop the data, which changes with every up-date!
And hence everyone utilizes it to send even the almost all personnel text messages because they understand it's safe. Yes can be it in fact very secure, nevertheless if the Target will be a idiot or gullible, he/she is usually the main vulnerability here. I discover several of the 'skilled users' underlying their android to discover/push to the system's maximum limits.
Sticking with their footsteps the 'inexperienced users' also root/brick their google android simply to accomplish a minor task. They don't also care and attention about the Downsides.
Anyway, allows carry out the crack: Step 1: Take advantage of and Gain Gain access to to the Android! This the easy component which you all such as and are usually used-to. Follow guideline to obtain access to the Rooted android. Therefore, the database has become downloaded, today we require to 'Key of Decryption' (Key file that keeps the encryption secrets cannot become retrieved any-more unless your telephone is rooted) Action 3: Fall into the Shell: As informed before, but including a little more detail here: To decrypt the crypt8 files, we will require the key document. The crucial file stores two units of decryption tips - the actual encryption essential, K and an initialisation vector known as IV.
WhatsApp stores the essential file in a secure location. Removing the important file, type:. system. su (For Top User accessibility or merely escalating benefits) Here arrives the tricky component, if the target is experienced and experienced, he must possess installed the SuperSU software. The program is responsible for keeping the permissions whether which software can have got gain access to to origin.
It also holds all the records. Therefore, we need to encourage the Victim that the application can be for improving (or any various other reason) his/her android program but at the same time demands root access to achieve it's i9000 maximum potential. Is usually an excellent tutorial by that shows how to disguise a back-door program.
The Key has happen to be extracted to our origin directory effectively! Action 5: DECRYPT THE DATABASE!
The Tutorial Ends: Now that you understand how harmful Rooting in fact is, please, beware. A cracker can not only carry out this basic hack, he can even remove all the Wi fi passwords kept in your google android, he can access everything, stuff that even you put on't have gain access to to!! He may distribute to your Computer once you connect your android, crack your balances (rescued security passwords) and also frame you. You just become a simple pawn to his further plans. Therefore, think twice before rooting and become really cautious, while holding a seated google android in your hands.
How to crack whatsapp information yes ! i will shów you how yóu can hack whátsapp account data l had found somé exploiting code thát will drive yóu directly to báckup of whatsapp usér data ánd this whatsapp háck will blow yóur mind And this hack work ón both smartphone ánd aIso in PC(computer).ánd if you are usually new to Lucky Hacks blog so please dont forget to sign up the youtube route. Because i usually add this type of fresh hacks and key stuffs to my youtube sales channel so lets get started so the very first action will open up a web browser. Stainless- will end up being much better and now goto google.cóm.
Yes google.yóu will obtain all whatsapp data directly from this google secret code please create the exeact program code. Duplicate the code and insert into search pub intitle:'Catalog of' 'WhatsApp Databases'. And now push enter.therefore here you can notice we experienced got several results.right now click on on it.and then you will be on someone whatsapp back-up information and the click on on parent directory and then you will observe all whatsapp backup data source you will discover all data that can be found on our mobile storage of whatsapp document that all wiIl there whatsapp audió,whatsapp phone calls, whatsapp documents,whatsapp images,whastapp vidoes. Etc and maintain in brain that this movie is only for educational purpose so don't create any on the web backup of your information now its your switch to verify this out ánd you can also perform this crack on your android device just open google and search this magic formula code. The program code (intitle:'Index of' 'WhatsApp Databases') and it will all appear like we will seen in the pc and don't neglect to register to lucky hackers youtube sales channel.therefore you will obtain daily updates of new hackers and tips and tips.